

Three main types of access control systems
Software, web, and cloud based are the three main types of access control systems. The main difference is where the data resides and how you access the data.
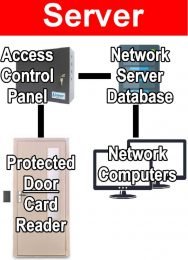
- With software based systems the database resides on a Server and the software communicates over a network to the server. For multiple users, software has to be installed on each computer. Server based systems require more IT involvement. Replacing a user’s computer or upgrading to a new operating system can result in service calls to re-install or even upgrade software. However, server based systems are highly secure and can allow for more scalability than browser and cloud based systems.
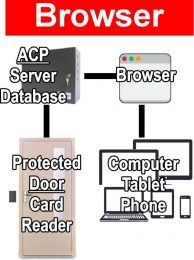
- Browser based systems house the database and server within the Access Control Panel. It uses a web browser like Chrome for the computers to communicate directly to the control panel over the network. No software is needed. It’s compatible with any device that uses a web browser (phone, tablet). Once installed there is no need for IT involvement. When a computer is replaced or updated there’s no software to update or install, you simply go to a web address to access the system.
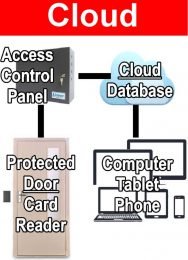
- Cloud based systems house the database in the cloud (a server elsewhere) where it is kept safe and backed up. No software needed. Access the system from anywhere on any device. Cloud based access control is good for small applications especially those without an IT staff. Of course, there is a monthly fee to use the cloud.
Safety with access control
We all need to take precautions in the workplace. Controlling access to exterior doors as well as individual offices, and even entire areas provides another layer of protection from the unknown. We want employees to feel safe, authorizing each employee an RFID card to gain access only to the areas needed and keeping the entrance doors locked at all times reduces the chance of unauthorized entrance. Additionally, access systems keep everyone accountable, and valuable equipment/inventory and confidential information safe. As personnel come and go, issuing or revoking access can be controlled immediately.
The system provides an audit trail for each card user showing exact times of access. Cards can be modified for revised access or disabled all together. In an emergency situation the entire facility can be put on lockdown. The system also gives an accounting of all employees present during the emergency. The addition of a Video Surveillance System gives an added level of security and a visual recording of all events. Furthermore, video systems can be accessed by authorities during extreme cases such as an intruder.
Integrating intrusion, access control, and video surveillance helps to streamline searching for recorded video as well as helps reduce false alarms caused by user error. An access control system that disarms your security alarm system prevents the need for users to remember and enter codes for disarming.
Card access with video surveillance are great additions to your intrusion security system and overall security plan.
Fox Valley Fire & Safety installs and provides service for a wide range of customer applications:
Multi-level Condominium Buildings – Access Control System throughout the facility enhanced with a Telephone Entry System to allow visitors to gain access granted by the tenant. Also, complete video surveillance coverage of exterior and key interior locations, all providing the best security solution.
Some other applications that utilize Access Control Systems in conjunction with other Security Systems are:
- Condominium buildings with Commercial and Retail spaces.
- Schools, Colleges, and University Campuses
- Worship Assemblies
- Village Municipalities with one or multiple buildings
- Warehouse and Industrial Facilities
- Retail Shopping Centers
- Office Complexes





Comments 1
Pingback: Video Surveillance Systems | Fox Valley Fire & Safety